Account Takeover Fraud: Building a FORTE Defense
Key Takeaways
- Account takeover (ATO) fraud is a business problem, not just a security issue: It drives direct losses, chargebacks and higher support volume while eroding trust in your portals and digital channels.
- The FORTE framework gives you a simple way to organize defenses: Firewall and front-door controls, OTP, risk-based monitoring, tokenization and encryption give risk and ops leaders a shared language to discuss gaps and priorities.
- You do not have to implement everything at once to make progress: Start by reviewing login flows, high-risk actions and how your payments partners handle tokenization and encryption, then build a phased roadmap to strengthen ATO defenses over time.
Account takeover (ATO) fraud is one of the most costly—and least visible—ways organizations lose customers and revenue. Instead of headline-grabbing breaches, ATO fraud often shows up as disputed payments, frustrated account holders and support teams left without answers. Why? Because on paper, the logins looked legitimate.
Attackers have learned that if they can get into a user’s account, they can move money, change contact details, enroll new cards and set up recurring payments—often without touching your core systems. That makes ATO fraud a high-impact threat for any organization that offers bill pay portals, customer portals or embedded payments inside software platforms.
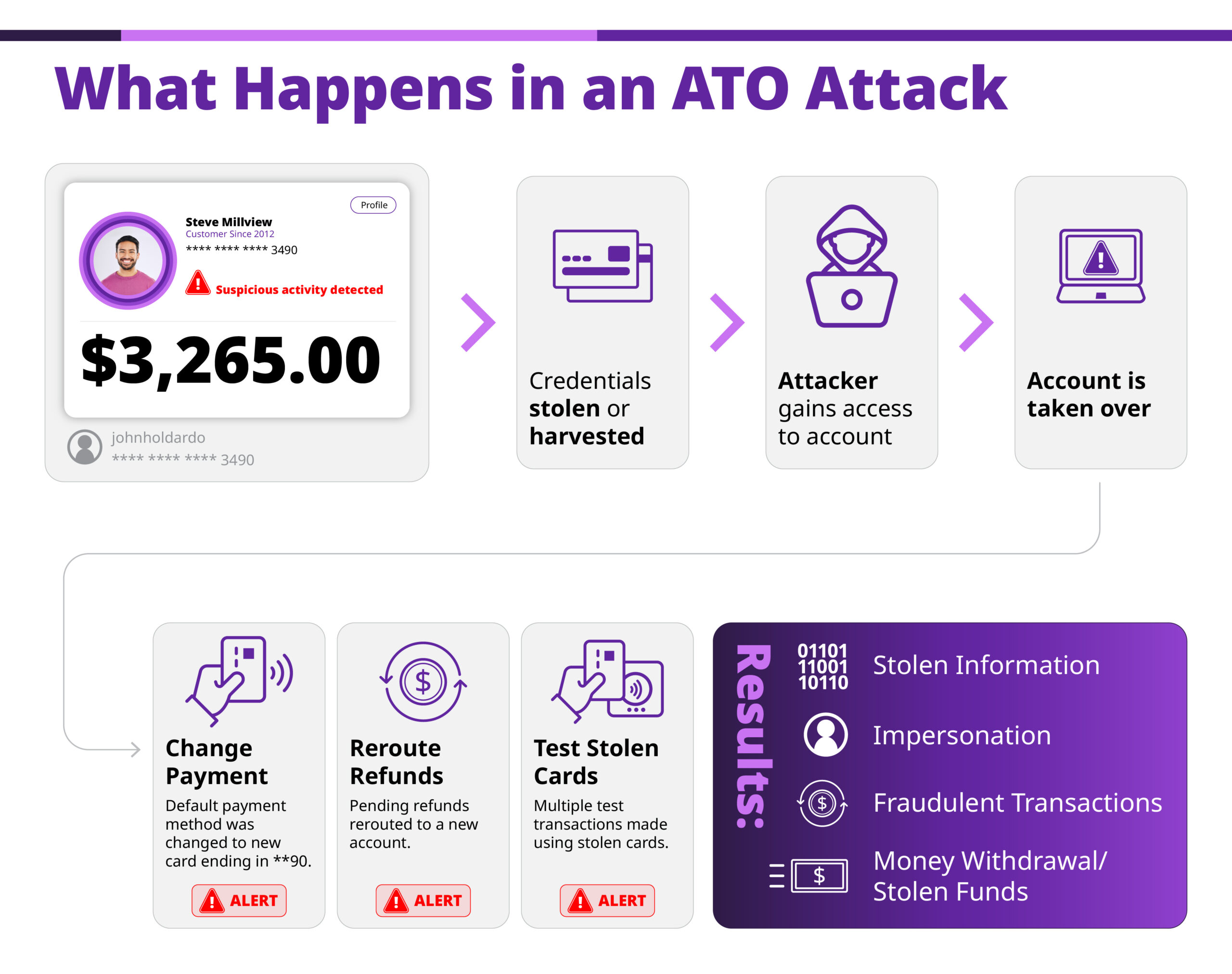
The FORTE framework introduced in this blog covers firewall protections, one-time passwords, risk-based monitoring, tokenization and encryption. This easy-to-follow framework gives risk, security and operations leaders a practical way to organize defenses. Read on to learn more.
The FORTE framework: 5 layers of ATO fraud defense
For risk, security and operations leaders, ATO fraud is a cross-functional problem. That is why it’s useful to have a simple way to explain defenses and tradeoffs to stakeholders who do not live in security tools all day. The FORTE framework is one way to do that.
F – Firewall and front-door controls: keeping bad traffic out
Your first line of defense is keeping obvious bad traffic away from your login pages and account features. You don’t need to be an infrastructure expert to understand the basics:
- Web application firewalls (WAFs) block common attack patterns and suspicious requests before they reach your application.
- Rate limits and velocity checks slow or stop bots that hammer your portal with credential stuffing attempts.
- IP reputation and geolocation filters flag traffic from known bad networks or regions where you have no legitimate users.
Together, these front-door controls reduce automated attacks that ever reach your authentication logic. They won’t stop a targeted phish against a specific user, but they make bulk ATO campaigns much harder and more expensive to run. A practical first step is to ask your teams and providers:
- Which WAF and front-door protections do we have in place today?
- How do we tune rate limits to avoid locking out real users while frustrating bots?
- How do we monitor for sudden spikes in login failures or suspicious requests?
O – OTP and stronger authentication: making stolen credentials less useful
If a password is the only barrier between an attacker and a customer account, you’re relying on the weakest link. Stronger authentication doesn’t have to add endless friction—it simply makes credentials alone insufficient for high-risk actions. Core options include:
- One-time passwords (OTPs) by SMS or email for logins from new devices or locations
- App-based or push authentication in a trusted mobile app
- Step-up checks for sensitive actions like changing payment methods, updating contact info or enrolling in autopay
Used well, these controls make ATO far harder because stolen credentials are less useful without access to a device or inbox. Good questions to ask include:
- Where do we use OTP or stronger factors today?
- Do we challenge only at login, or also for high-risk actions?
- How often do users abandon sessions due to friction?
The goal is to balance friction with risk.
R – Risk-based monitoring: spotting suspicious behavior before it becomes loss
Even with strong front-door controls and OTP, some takeover attempts will slip through. Risk-based monitoring helps catch them by assigning risk scores based on behavior and context. Key signals include:
- New devices or browsers
- Logins from unusual locations or networks
- Sudden shifts like many failed logins, rapid password changes, or adding multiple new payment methods
With these signals, you can:
- Prompt for extra verification when risk is high
- Flag sessions for manual review
- Temporarily limit high-value payments or changes to stored data
Behavioral analytics, device intelligence and simple rules can all support this layer. The goal is to move from a one-time yes/no login decision to an ongoing evaluation of whether a session still looks legitimate.
T – Tokenization: limiting the damage if accounts or data are compromised
No defense is perfect. If an attacker does manage to take over an account, the question becomes how much damage they can actually do. Tokenization helps answer that question in your favor.
Instead of storing raw card numbers or other sensitive payment details in your systems, tokenization replaces that data with tokens that are useless outside a specific context. A token replaces the underlying card information when you initiate payments, yet the actual card number lives in a secure vault managed by a trusted provider.
For account takeover scenarios, tokenization offers several advantages:
- Even if an attacker gains access to an account, they cannot see or exfiltrate raw card data.
- Backend systems that only work with tokens hold less sensitive information, reducing the blast radius if something goes wrong.
- You can revoke or rotate tokens without forcing users to reenter full card details in many cases.
In a world where ATO is a persistent threat, limiting what an attacker can steal if they get in is just as important as keeping them out in the first place.
E – Encryption: protecting data in motion and at rest
For ATO, encryption matters in several ways:
- Transport-level encryption (such as TLS) ensures that credentials and session cookies are not exposed to eavesdroppers as users log in or perform actions
- Database and disk encryption make it harder for attackers to read sensitive data if they gain access to infrastructure or backups
- Key management practices determine how easy it would be for a criminal to misuse encrypted data if they obtain partial access
When combined with tokenization, strong authentication and risk-based monitoring, encryption helps ensure that even successful account takeovers do not automatically turn into catastrophic data breaches.
Practical steps to strengthen your ATO defenses
No organization flips a switch and implements every element of the FORTE framework overnight. The point is not perfection. It is clarity.
The important thing is to move deliberately. ATO fraud is not going away, but you are not starting from zero.
If you rely on a payments platform or embedded payments provider, bring them into the conversation early. Ask how they support FORTE-style defenses and where they can take work off your plate so your teams can focus on the parts of account takeover fraud defense only you can own.
Taking these steps not only protects your customers and sensitive data, but also empowers your organization to outsmart fraudsters at every turn—because building your fraud-fighting FORTE is the strongest move you can make in today’s threat landscape.
Get Protected with CSG Forte
Ready to put FORTE to work and fortify your defenses against account takeover fraud? Check out what CSG PaymentsProtection.ai can do for you, then reach out to talk to the experts at CSG Forte to learn how to implement firewall protections, OTP authentication, risk-based monitoring, tokenization and encryption.
FAQS
Q1: What is account takeover fraud?
Account takeover fraud happens when a criminal gains control of a legitimate user’s account and uses it to make changes or perform transactions without permission. Instead of breaking your systems, they log in with stolen or guessed credentials, then update contact details, swap stored payment methods or move money. Because the activity often looks like a normal login, ATO can be hard to spot until customers complain or losses pile up.
Q2: How do you prevent account takeover fraud?
Preventing account takeover fraud starts with hardening the front door, then layering in smarter checks as activity unfolds. That means putting controls like web application firewalls, rate limits and IP reputation in front of your portals, then adding stronger authentication such as OTP or step-up challenges around high-risk actions. From there, risk-based monitoring, tokenization and strong encryption help reduce both the likelihood and the impact of ATO when it does occur.
Q3: How do you stop account takeover fraud in real time?
Stopping ATO in real time depends on your ability to spot risky sessions quickly, not just bad passwords. Risk-based monitoring that looks at device, behavior, location and velocity can flag suspicious logins or actions as they happen, then trigger extra verification, temporary limits or blocks. When your payments platform and security tools work together, you can challenge or shut down high-risk activity before it turns into confirmed loss.
Q4: How can enterprises prove account takeover fraud prevention reduces losses?
Enterprises can show the impact of ATO defenses by tying security metrics to business outcomes. That includes tracking ATO attempts versus successful takeovers, measuring changes in fraud write-offs and chargebacks over time and comparing loss rates before and after key controls like OTP, behavioral analytics or tokenization go live. When you line those numbers up with support volume and customer complaints, it becomes much easier to show how account takeover fraud prevention contributes directly to lower losses and a healthier digital business.










