How to Improve Payments Customer Portal Security
Key Takeaways
- Customer portals that touch payments or sensitive data concentrate risk across account takeover, card testing, ACH abuse, refund schemes, and data theft—so they need a layered security model, not just stronger passwords.
- The most effective programs protect the front door (login), high-risk actions (account changes, payments, refunds) and the data layer (tokenization, encryption), guided by risk-based monitoring across sessions and transactions.
- AI-driven, cross-channel monitoring like CSG Payments Protection.ai can close visibility gaps across ACH, cards and digital wallets and help reduce fraud losses and false positives while keeping approvals flowing.
Customer portals have become the default way customers pay bills, update details, and manage services. That convenience is exactly why portals are now some of the highest-value assets in your business—and some of the highest-value targets for fraud.
When a single login can unlock saved payment methods, refunds, credits, and sensitive account data, attackers don’t need to “hack your systems.” They just need to behave like a plausible customer.
This article introduces a big-picture framework for customer portal security—especially for portals that touch payments or high-value data. It’s designed for risk leaders who need to see how identity, payments, fraud, and customer experience fit together, and where AI-powered protection like CSG Payments Protection.ai can strengthen defenses without stopping good business.
Why customer portals are prime fraud targets
Customer portals concentrate three things modern fraudsters care about most:
Money movement in a low-friction channel
From the attacker’s perspective, portals are a fast way to:
b. Make one-time or recurring payments
c. Request refunds or credits
d. Redeem loyalty balances or incentives
Because these actions are supposed to be self-service and low friction, they’re often less scrutinized than back-office changes.
Long-lived, trusted accounts
An established customer account with stored payment methods, predictable billing, and a history of on-time payments is more valuable than a single stolen card. A compromised account can be used to move money, test instruments, or harvest data over time, often without triggering obvious alarms.
High-value personal and payment data
Even when portals don’t store full payment credentials, they often hold identity data (names, addresses, contact details) and partial payment information that can be combined with other breaches. That makes them useful both for direct financial fraud and for building synthetic identities.
Automation-friendly surfaces
Login pages, password reset flows, and payment forms are attractive to bot operators. Attackers can run automated scripts to test large credential lists, push small card authorizations, or probe forms for weak validation and error handling.
Success looks like normal use
Unlike obviously malicious traffic, portal fraud often mimics legitimate journeys—log in, view a bill, make a payment, change an address. The difference is in signals like device, location, velocity, and behavior patterns—not in the steps themselves.
Building a layered defense for login and payments
No single control will address all of these risks. Effective customer portal security is about building a layered model that protects:
- The front door (login and account recovery)
- High-risk actions in the session (account changes, payments, refunds)
- The data layer (how and where sensitive information is handled)
- Detection and response (how quickly you see and act on anomalies)
A practical way to think about layers:
- Identity and authentication
- Session and behavior monitoring
- Payments and refunds controls
- Data protection
- Operations and continuous improvement
1) Identity and authentication: protect the front door and the keys
Start with strong, well-understood basics:
- Password hygiene and breached-password checks so obviously weak or known-compromised passwords are rejected.
- Secure account recovery that protects email/phone changes and reset flows at least as much as initial login.
- Rate limiting and bot controls at login and recovery endpoints to slow credential stuffing and scripted abuse.
Then move beyond all-or-nothing MFA to risk-based step-up:
Map your portal into risk tiers—for example:
- Low-risk: viewing bills or read-only pages
- Medium-risk: viewing statements, updating non-critical profile fields
- High-risk: changing email/phone, adding or changing payment methods, turning on autopay, initiating large or unusual payments, requesting refunds
Require additional verification (MFA, one-time passwords, push approvals, or similar) when:
- A session attempts high-risk actions
- The device or location is new or suspicious (“impossible travel,” TOR/VPN use, emulator signals)
- Behavior or velocity looks abnormal for that user
This “right-sizing authentication and challenges” approach reduces ATO risk while avoiding blanket friction that drives abandonment.
2) Session and behavior monitoring: watch what happens after login
Modern fraud programs treat login as the start of evaluation, not the end. Risk-based monitoring looks across sessions and transactions to separate normal from risky activity, using a mix of rules, device intelligence, and behavioral analytics.
Useful signals include:
- Device: new vs. known device, emulator indicators, rooted/jailbroken status
- Network: IP reputation, proxies/VPNs, unusual ASNs or geographies
- Behavioral: typing cadence, copy-and-paste usage in forms, page navigation patterns, time on page
- Velocity: rapid-fire attempts, repeated failures, fast chaining of sensitive actions
- Account history: recent password resets, multiple contact-detail changes, sudden change in typical payment amounts or timing
You can then define risk scores or tiers that drive real-time actions:
- Allow low-risk sessions to proceed with minimal friction
- Add challenges for medium-risk sessions at sensitive steps
- Block, delay, or route to review for high-risk sessions and actions
This is also where AI-based tools start to matter: watching patterns across many sessions and payment events to spot emerging threats that simple rules miss.
3) Payments and refunds: treat money movement as its own layer
Payments and refunds deserve specific controls on top of general account security. Focus on key chokepoints in your flows:
- Adding or updating payment methods (card or ACH)
- First payments from a new device or new funding source
- Unusually large or out-of-pattern payments
- Turning autopay on or off
- Initiating refunds or credit balance withdrawals
Practical measures include:
- Velocity controls and limits per account, device, IP, card, and bank account (e.g., caps on attempts per hour, limits on high-risk combinations like “new card + large payment”).
- ACH account validation at first use and whenever account numbers change, in line with Nacha expectations for online debits.
- “Refund to original method” as a default with tightly controlled exceptions and documented approvals, to reduce rerouting scams.
- Clear transaction logging that correlates payment events with account changes (e.g., password reset → email change → new bank account → refund request).
For many organizations, this layer is where adding an AI‑driven fraud engine can deliver outsized value—by analyzing ACH, card, and digital wallet transactions in near real time, spotting patterns consistent with card testing, refund abuse, or ATO‑driven payments.
4) Data protection: minimize what’s exposed and where
Even the strongest ATO defenses can’t eliminate all compromise risk. You also need to limit what an attacker can get if they do get in. Internal guidance on payment data security highlights several priorities:
- Data minimization: Don’t store payment or account data you don’t truly need. Avoid retaining full PAN or unnecessary sensitive authentication data.
- Tokenization: Replace card and bank details with tokens so your systems never store or transmit raw credentials. If an account or database is compromised, tokens are useless without the secure vault that maps them.
- Encryption: Use strong encryption in transit (e.g., TLS) and at rest for any store that contains sensitive identifiers, and manage keys with strict access and rotation controls.
- Access control and segmentation: Apply least-privilege access to admin tools and data stores, segment payment environments, and keep raw payment data in a PCI DSS-compliant enclave where possible.
Working with providers that offer PCI-validated tokenization, hosted payment pages, and secure storage can significantly reduce your own PCI scope and the blast radius of any incident.
5) Operations and continuous improvement
Controls are only as strong as the processes around them. High-performing teams treat portal security as an ongoing program, not a one-time project.
Metrics that tie to business outcomes
- Confirmed and suspected ATO incidents
- Login success and challenge rates, segmented by risk tier
- Payment approval and decline rates, including ACH returns
- Chargeback and dispute rates, refund ratios, and “friendly fraud” indicators
Playbooks for fraud spikes
Define clear steps for detecting, triaging, and responding to sudden fraud spikes—credential stuffing, card testing waves, or refund abuse—before they damage revenue and reputation.
Regular tuning cycles
Review rules, thresholds, and machine-learning outputs with fraud, payments, and CX stakeholders. Adjust controls as new patterns emerge and as you see where friction is hurting good customers.
Aligning fraud, security, and customer experience teams
Portal security fails most often at the seams—where fraud, security, payments, and customer experience each optimize for their own metrics. Internal planning guidance for this pillar emphasizes cross-functional alignment as a core success factor.
Four practical alignment moves:
1) Define high-risk actions together
Use a shared workshop to map high-risk actions across login, account management, and payments. Agree on which events should always trigger step-up, which should be risk-based, and which can stay low friction.
2) Set a “friction budget”
Instead of arguing abstractly about “too much MFA,” define acceptable challenge rates, abandonment thresholds, and support-call impacts by segment. Use monitoring data to see whether you’re hitting those targets.
3) Give customer service real visibility
Customer service teams are often the first to hear about ATO or blocked payments. Equip them with:
- A simple view of recent logins, device changes, and payment attempts
- Clear scripts for explaining extra verification
- Guardrails for handling refunds and overpayments within policy
4) Treat vendors as part of your control surface
Your identity provider, payments platform, fraud tools, and analytics stack all shape your security posture. Regularly review settings, logs, and roadmaps with them instead of assuming default configurations are enough.
Where Payments Protection.ai fits in your portal strategy
All of the layers above become more effective when you can see payment risk clearly across rails (card, ACH, digital wallet) and channels (web, mobile, IVR, assisted). That’s the gap CSG Payments Protection.ai is designed to fill.
Payments Protection.ai is a next-generation, AI-powered fraud detection and financial risk management solution that:
- Monitors ACH, card, and digital wallet transactions across online, phone, and in-person channels in near real time
- Uses AI/ML models and adaptive rules to identify patterns consistent with account takeover, card testing, refund abuse, merchant-level fraud, and other payment-risk scenarios
- Delivers industry-tuned protection and significantly reduces false positives, helping keep friction low for legitimate customers
- Operates on secure, PCI-compliant infrastructure with high availability, so protection scales with your traffic
In a portal context, that means you can:
- Add an intelligence layer over your existing identity and payment flows
- Correlate account events and payment events when evaluating risk
- Intercept suspicious transactions for review or decline, without rewriting your entire portal stack
If you’re evaluating your portal’s fraud and security posture, this framework can serve as a cross-team workshop agenda—and Payments Protection.ai can provide the AI-driven risk layer that keeps fraud in check while your best customers glide through the experience.
Ready to strengthen your portal’s defenses and deliver a seamless customer experience? Contact us today to learn how Payments Protection.ai can help your organization stay ahead of evolving fraud threats, simplify compliance, and ensure your customers’ trust at every transaction.
Frequently asked questions
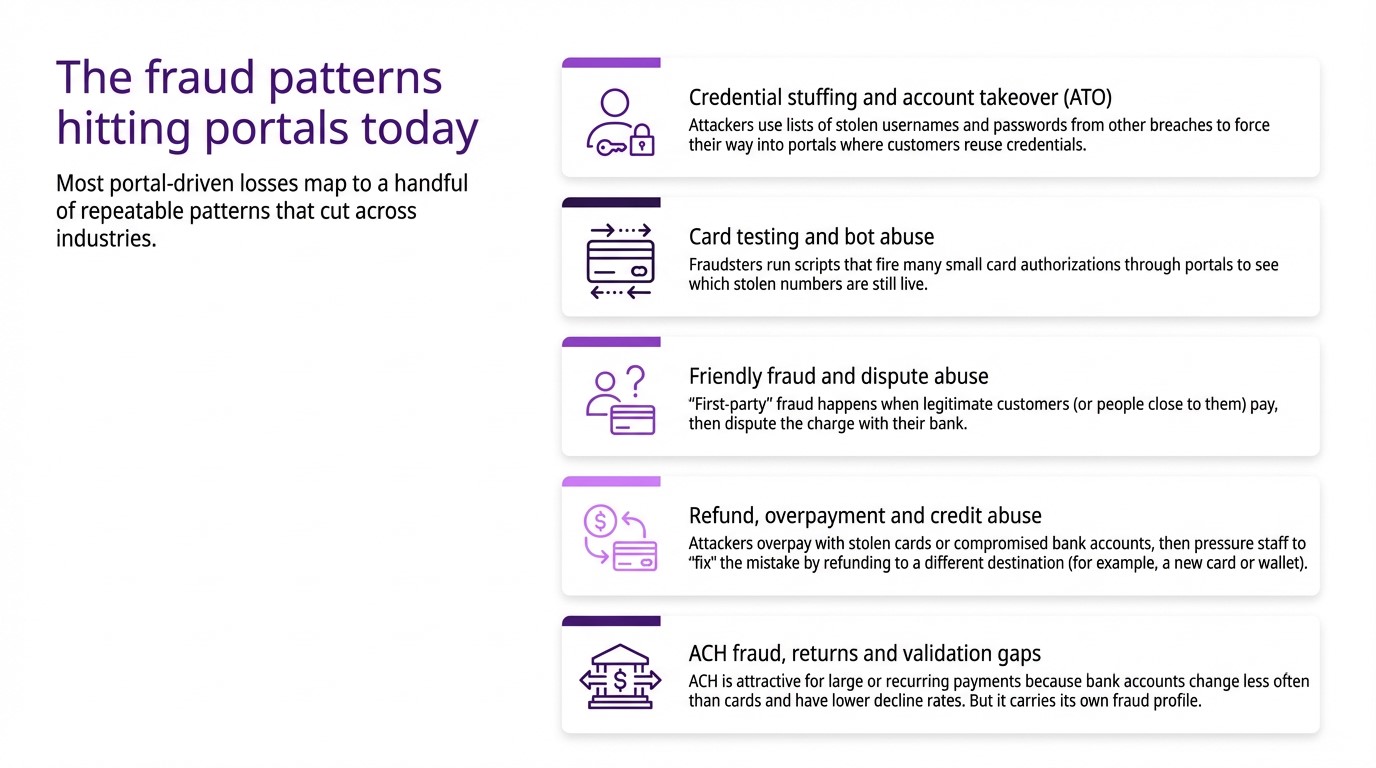
What are the most common fraud threats to customer portals that handle payments?
Customer portals are typically targeted by credential stuffing and account takeover attacks, card testing bots, friendly fraud and dispute abuse, refund and overpayment scams, and ACH abuse such as unauthorized debits or repeated NSF returns.
How is ACH fraud different from card fraud in a portal context?
Card fraud often appears as card-not-present misuse, card testing and disputed charges, while ACH fraud shows up as unauthorized debits, repeated NSF/return loops or invalid account details used to delay true payment; Nacha expects online ACH debits to be covered by a “commercially reasonable fraudulent transaction detection system” that includes account validation at first use and when account numbers change.
How can we fight portal fraud without over-blocking good customers?
Use risk-based, layered controls instead of blanket rules: MFA or one-time passwords for higher-risk actions, tuned velocity rules and bot controls, ACH account validation on new or changed bank details and clear refund policies—while allowing low-risk recurring payments and routine logins to flow with minimal friction.
Where do tokenization and encryption fit in customer portal security?
Tokenization replaces raw card or bank data with non-sensitive tokens, so even if an account is compromised attackers cannot exfiltrate usable payment credentials; encryption protects sensitive data in transit and at rest and supports PCI DSS and Nacha data-protection expectations.
How does CSG Payments Protection.ai help with customer portal security?
CSG Payments Protection.ai is a SaaS-based fraud detection and financial risk-management solution that monitors ACH, card and digital wallet transactions across online, phone and in-person channels in near real time to detect patterns like account takeover, card testing, refund abuse and merchant bust-out, complementing your portal-level controls.